
Data Protection / Privacy Policy
- HOME >
- Data Protection / Privacy Policy >
- Information Security Policy
Information Security Policy
Policy/Philosophy
Our Group considers the protection of the information assets of our Group and our customers and business partners as important issues of management and follows laws/regulations and company regulations, and at the same time we share the significance and responsibility of management of information assets with our employees and manage information assets in an appropriate manner based on the following policy.
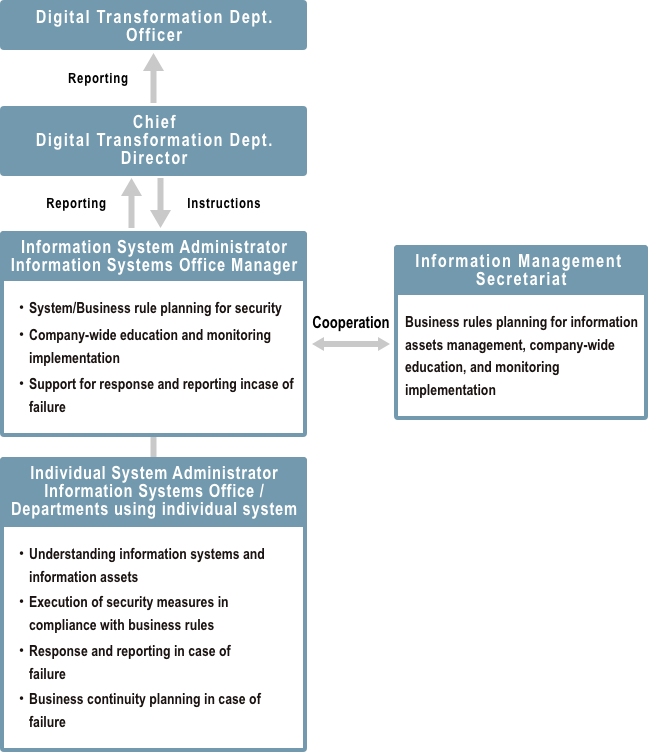
1.Development of the information security structure
Our Group shall develop the information security management structure and work on appropriate management of information assets.
Information Security System
2.Information security measures
Our company group shall work on prevention of the occurrence of information security related incidents through by implementing multifaceted security measures, including organizational and Process and system measures.
Examples of security measures implemented
| Measure Classification | Details of Measures |
|---|---|
| Organization |
|
| Process |
|
| System |
|
| Partner |
|
- 1 IPS:Intrusion Prevention System
- 2 MSS:Managed Security Service
3.Handing information security incidents
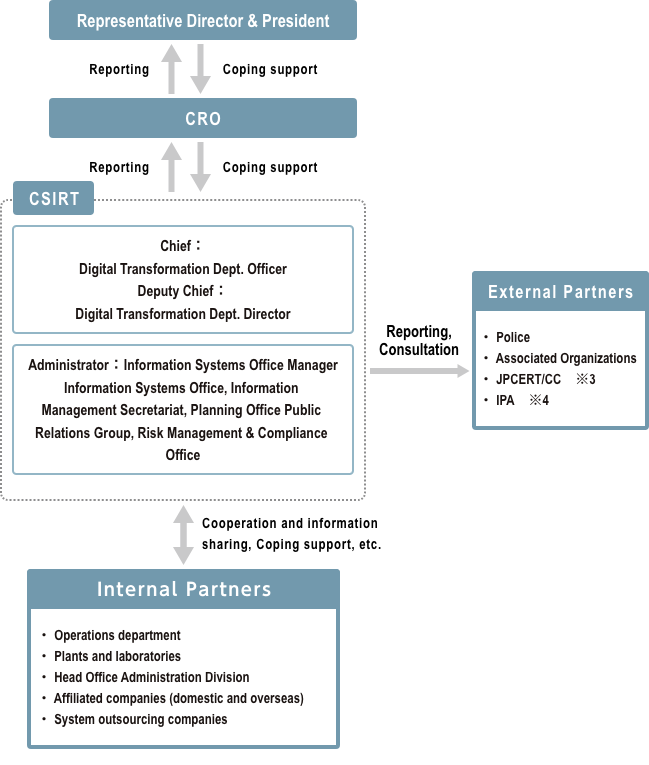
If an information security incident occurs, our Group shall use the countermeasures in an appropriate and prompt manner to minimize damage and we shall work on re-occurrence prevention measures.
If an information security incident occurs, we will establish a CSIRT (Computer Security Incident Response Team) to quickly and accurately disclose information to all stakeholders and strive to bring the incident under control as quickly as possible.
Security Incident Response System
- 3 JPCERT/CC:Japan Computer Emergency Response Team Coordination Center
- 4 IPA:Information-technology Promotion Agency, Japan
4.Education regarding information security
Our Group shall conduct educational/enlightenment activities regarding information security on a regular basis in order for employees to use and manage information assets in an appropriate manner.
5.Continuous improvement
Our Group shall continue improvement of information security management structure and countermeasures taking into account the environment surrounding management and social situation.
End of document





